C++ code (TSF.c) Compiling this code using the command 'gcc TSF.c -z... | Download Scientific Diagram

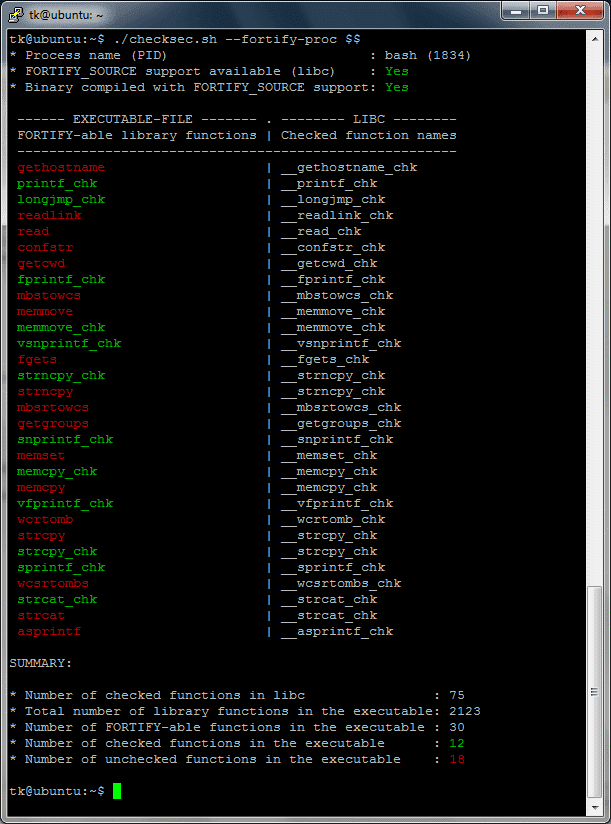
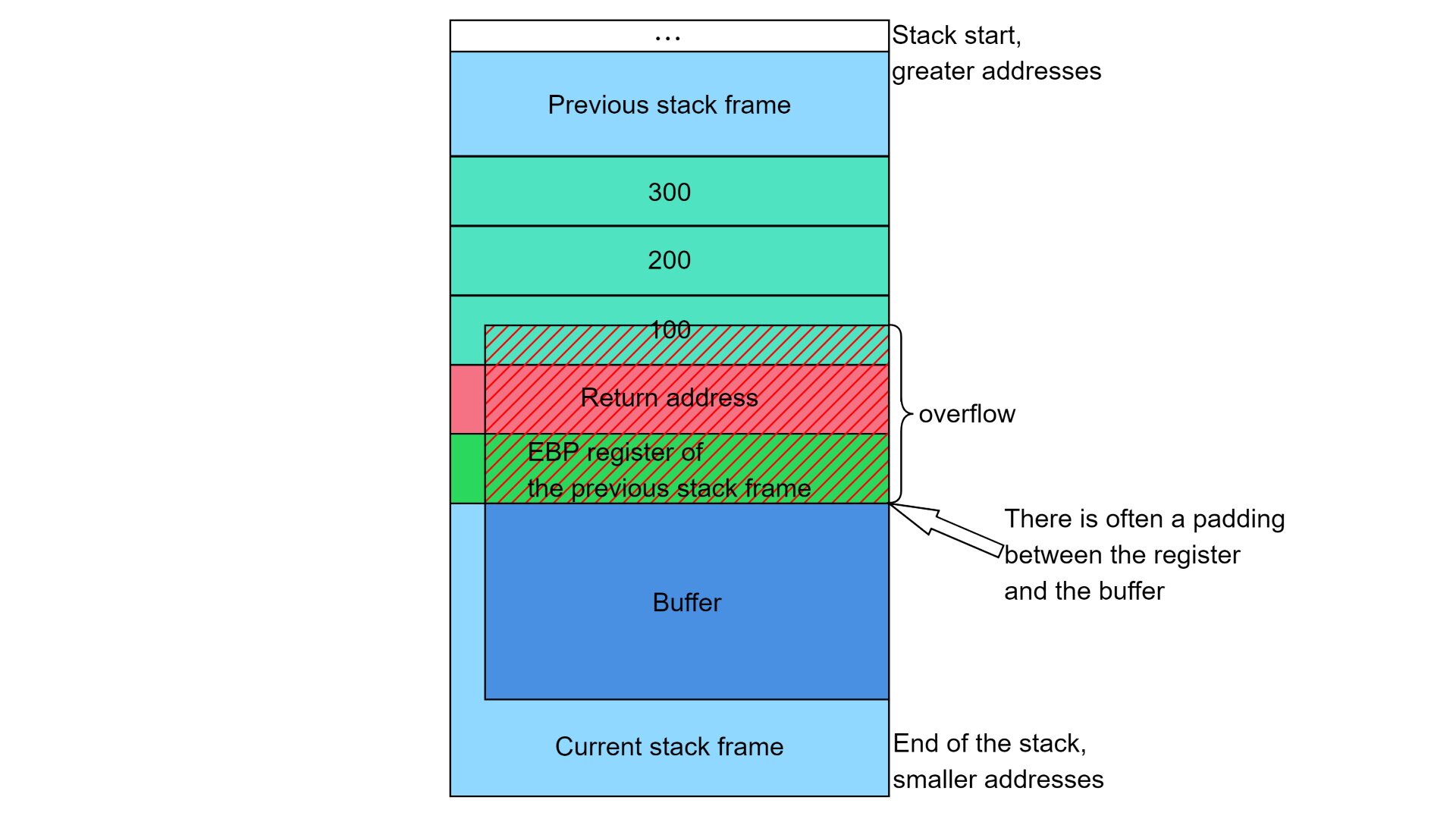
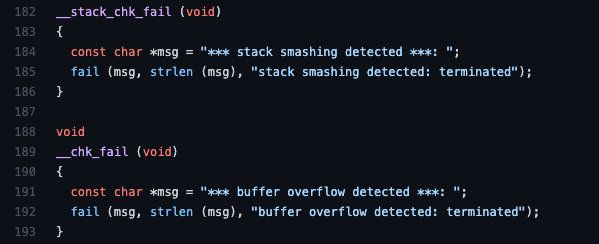
Stack buffer overflow protection 學習筆記– Stack canaries mechanism in User space – SZ Lin with Cybersecurity & Embedded Linux
x86 stack protector code references @GOTPCREL and @PLT even when built with -fno-pic or -fno-pie · Issue #62481 · llvm/llvm-project · GitHub
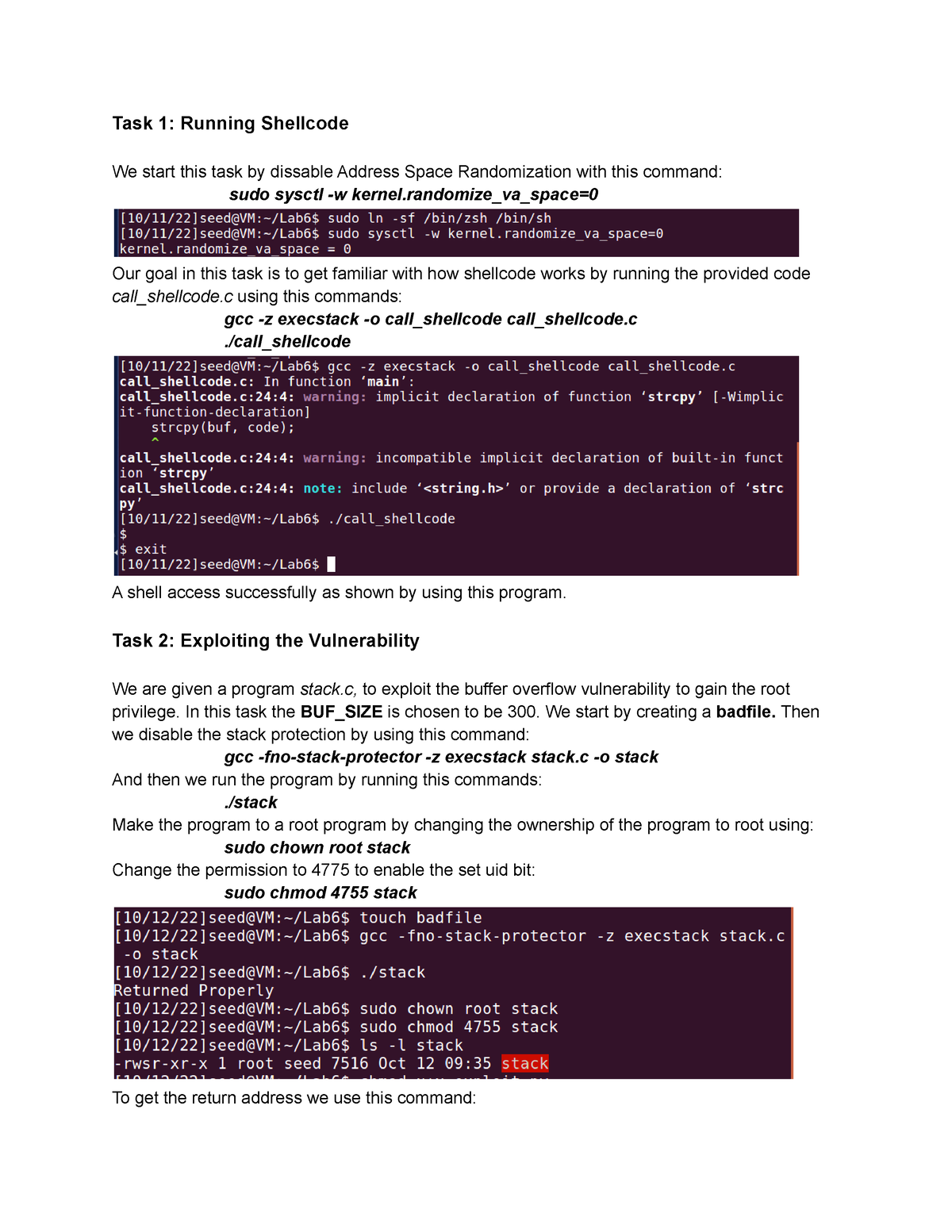
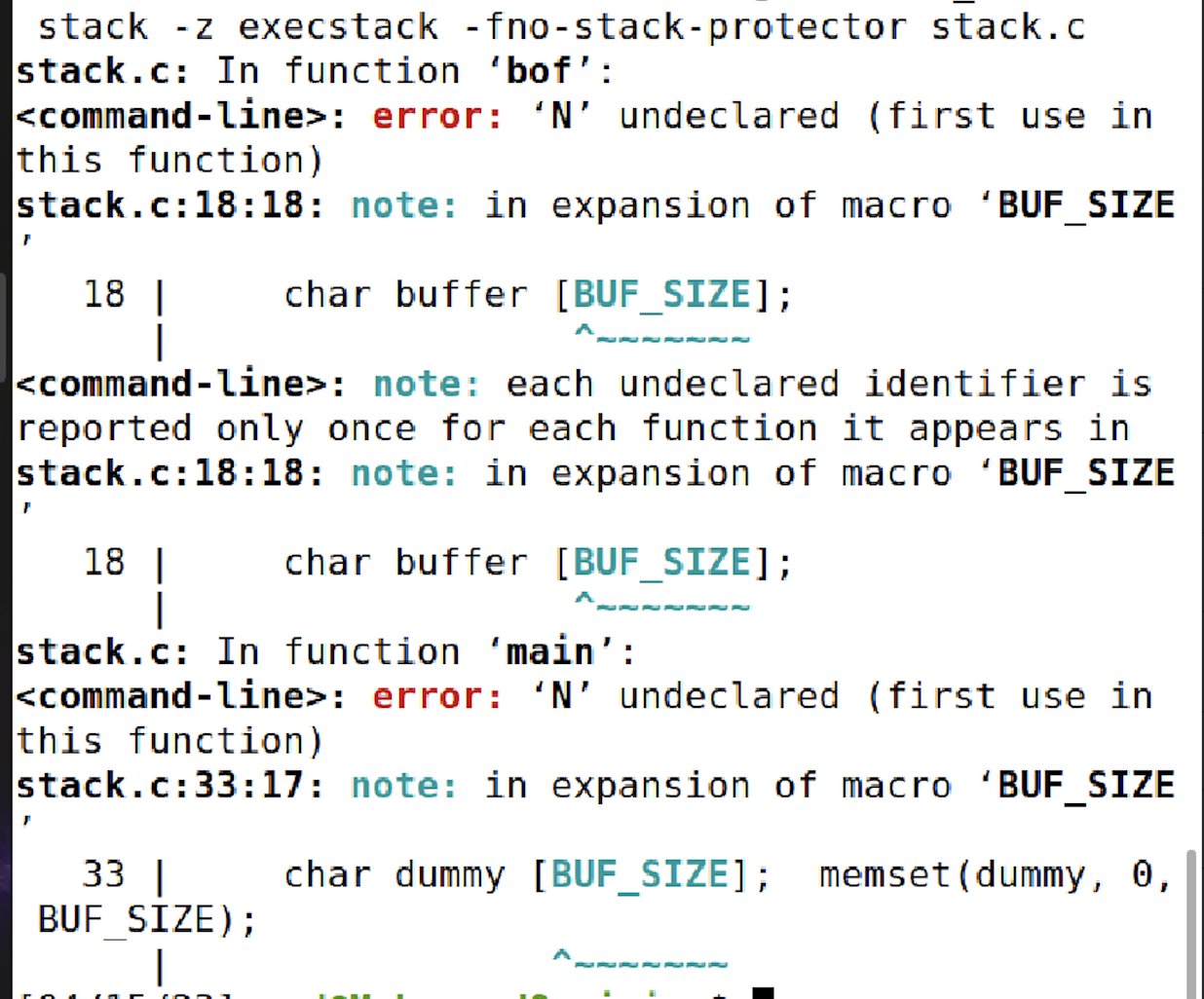
Buffer-Overflow Vulnerability Lab 6 - Task 1: Running Shellcode We start this task by dissable - Studocu